Network Models and Protocols
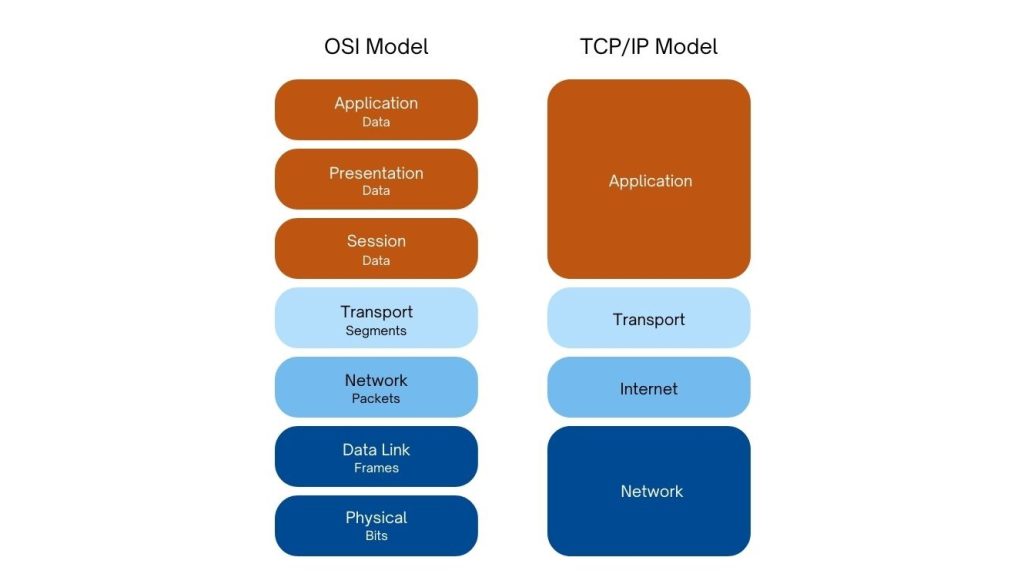
Behind the scenes, these models illustrate how each layer contributes to data transmission and the end user view and experience. We can look at these layers top-down (application to physical) or bottom-up (physical to application). In this introduction, let’s look at the layers bottom-up through the OSI seven-layer model. We will explain each of these layers in further detail in the chapters of this part. Watch this video for an overview of the OSI model first [21].
Imagine you’re sending an email with an attachment to a colleague across the world. As you hit ‘send’ on your physical device, your email message is transformed into electrical signals or radio waves, ready to travel across cables or airwaves. Moving up to the data link layer, your email packets are equipped with physical addresses, known as MAC addresses. These addresses help guide the packets through switches, bridges, and/or routers within your local network. Once organized, the packets ascend to the network layer. Here, devices called routers utilize IP addresses to direct the packets across the global network, enabling your email to cross geographical boundaries. Now, your email enters the transport layer. Here, the message is divided into manageable packets, ensuring efficient transmission.
The final three layers in the OSI Model are grouped together in the Internet Model, and prepare the data for the user. The session layer manages the dialogue control, guaranteeing that the packets are transmitted cohesively, maintaining the integrity of the email conversation. As the data proceeds to the presentation layer, any necessary encryption or compression is applied. This layer ensures that your email’s content remains secure and can be properly understood by both sender and receiver. Finally, the data arrives at the topmost layer, the application layer. Here, your email client, armed with protocols such SMTP and IMAP, initiates the sending process.
This journey reveals how a simple email is sent through the orchestration of layered protocols, through several technical processes. In this section, as we explore the mechanisms behind these communication layers, you will undoubtedly gain a new appreciation for the meticulous underpinnings that enables the digital connectivity we often take for granted.
References:
[24] “OSI Model Layer Attacks, Mitigation & Protocols .” YouTube, Cyber Gray Matter, 2022. Available: https://www.youtube.com/watch?v=CYhpEr8GFok

